In Africa’s booming tech and fintech landscape, global reach is the objective. But with international users comes international regulation. The General Data Protection Regulation (GDPR), far from being just a European directive, has established a global benchmark for data privacy that directly impacts any African company targeting customers or processing data from the European Union. Overlooking its mandates can lead to significant financial penalties, a severe erosion of customer trust, and exclusion from lucrative international markets.
This article provides more than just a surface-level overview; it is a definitive GDPR compliance checklist crafted specifically for the operational realities of African technology and fintech innovators. It serves as a practical, step-by-step roadmap to navigate the complexities of data protection. By following this guide, you will not only achieve compliance but also strategically build a robust data privacy framework that acts as a powerful competitive differentiator.
We will move beyond generic advice to deliver actionable insights and implementation details tailored to the unique challenges and opportunities within Africa’s dynamic digital economy. This checklist breaks down the core requirements into manageable tasks, including:
- Data Mapping and Inventory: Understanding what data you hold and where it flows.
- Lawful Basis Documentation: Justifying every data processing activity.
- Privacy Notices: Communicating transparently with your users.
- Data Subject Rights: Building systems to honor user requests.
- Data Protection Impact Assessments (DPIAs): Proactively managing high-risk processing.
- Breach Notification: Preparing for and responding to incidents effectively.
- Vendor Management: Ensuring your partners are also compliant.
- Security Measures: Implementing technical and organizational safeguards.
Let’s begin constructing your foundation for global trust and sustainable growth.
1. Data Mapping and Inventory
Before you can protect personal data, you must first know what data you have, where it is, and what you’re doing with it. This foundational step, known as creating a Data Map and Inventory, is the bedrock of any successful GDPR compliance checklist. It involves a comprehensive audit and documentation of all personal data your organization collects, processes, and stores.
Think of it as creating a detailed blueprint of your data ecosystem. This process identifies data sources (e.g., app sign-up forms, CRM systems), the purpose for processing (e.g., payment processing, marketing), internal and external data flows, retention periods, and any third-party sharing agreements. For African fintechs handling sensitive financial information or tech startups scaling rapidly, this visibility is non-negotiable. It moves compliance from a vague concept to a manageable, documented reality.
The Value of a Comprehensive Data Inventory
A thorough data inventory is not just a compliance task; it’s a strategic business asset. It enables your organization to respond efficiently to Data Subject Access Requests (DSARs), conduct accurate Data Protection Impact Assessments (DPIAs), and ensure that data processing activities have a clear legal basis.
Key Insight: Without a clear data map, you are essentially flying blind. You cannot apply security measures, honor data subject rights, or demonstrate accountability to regulators if you don’t have a granular understanding of your data landscape.
Tech giants like Microsoft and Salesforce exemplify this principle through meticulous data mapping. They maintain detailed records of customer data flows across their vast service ecosystems, enabling them to manage risk and build trust. For an African startup, this might mean mapping user data from a mobile money app, through a third-party payment gateway, and into a cloud storage server, documenting each stage of the journey.
Implementing Your Data Mapping Strategy
To begin, start with your most critical data processing activities. Focus on high-volume or high-risk areas first, such as payment transactions or customer onboarding.
- Involve Cross-Functional Teams: Engage stakeholders from every department, including marketing, engineering, HR, and legal. Each team has a unique perspective on the data they handle.
- Use Automation: Leverage automated data discovery tools to scan your networks, databases, and cloud environments to identify where personal data resides.
- Visualize the Flow: Create visual data flow diagrams to make complex processes easier to understand for both technical and non-technical stakeholders.
- Establish Regular Reviews: Your data ecosystem is not static. Set up a recurring schedule (e.g., quarterly or biannually) to review and update your data inventory, especially after launching new products or features.
The following infographic illustrates the core workflow for establishing your data inventory.
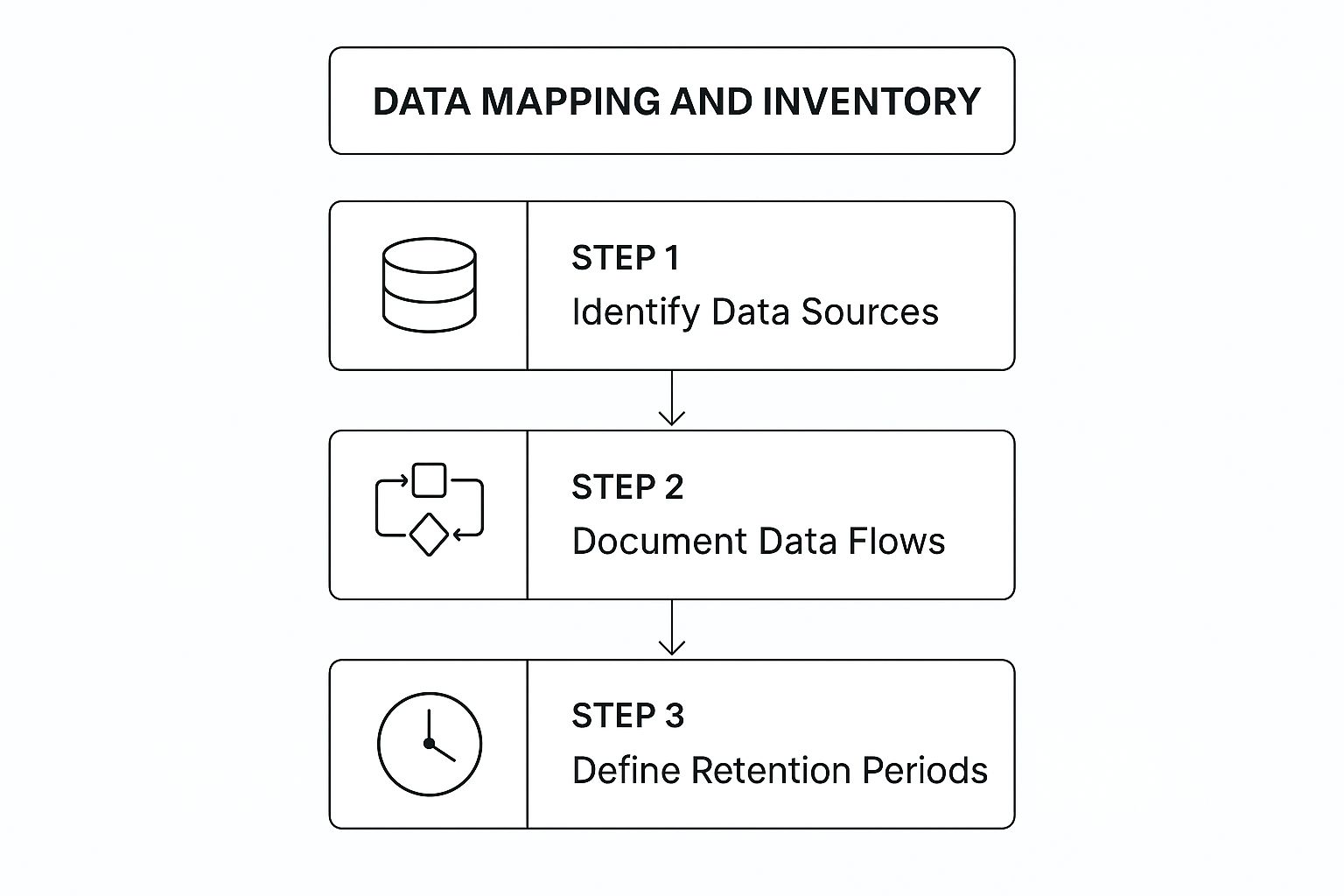
This process flow highlights the logical progression from discovering data to understanding its lifecycle, forming a crucial part of your GDPR compliance checklist.
For a deeper dive into the legal and practical aspects of data mapping, the video below offers expert insights.
2. Lawful Basis Determination and Documentation
Under GDPR, you cannot process personal data just because you want to. Every single data processing activity must be justified by a specific, valid legal reason. This critical step, Lawful Basis Determination and Documentation, requires organizations to identify, implement, and record the appropriate lawful basis for each way they use personal data.
This is not a mere formality; it is the legal pillar upon which your data processing stands. You must determine which of the six lawful bases applies, document this decision, and communicate it clearly to data subjects in your privacy notice. For African fintechs processing Know Your Customer (KYC) data or tech startups using data for marketing, proving you have a valid reason is fundamental to your GDPR compliance checklist.
The Value of a Documented Lawful Basis
Properly determining and documenting your lawful basis is essential for accountability and transparency. It demonstrates to regulators that your processing is fair and lawful, and it builds trust with users by explaining why you need their data. It also forces internal discipline, preventing “data hoarding” or processing without a clear, legally sound purpose.
Key Insight: Choosing the right lawful basis is a strategic decision, not an administrative one. Relying on the wrong basis, such as using consent when another is more appropriate, can invalidate your processing and lead to significant compliance failures.
For instance, a banking institution relies on the ‘legal obligation’ basis for KYC checks mandated by anti-money laundering regulations. In contrast, Google often uses ‘legitimate interests’ for personalizing advertising, a process that requires a careful balancing test against individuals’ rights. An African e-health startup might use ‘vital interests’ to process a patient’s data in a life-or-death emergency without their explicit consent.
Implementing Your Lawful Basis Strategy
Your data map from the previous step is the starting point. For each processing activity identified, you must now assign and document a lawful basis.
- Document Your Assessments: If you rely on ‘legitimate interests’, you must perform and document a Legitimate Interests Assessment (LIA) to demonstrate that your interests are not overridden by the rights of the data subject.
- Avoid Over-relying on Consent: Consent can be withdrawn at any time. For essential processing activities, consider if ‘performance of a contract’ or ‘legal obligation’ is a more robust and appropriate basis.
- Consider Data Subject Expectations: The basis you choose should align with what the individual would reasonably expect. Processing data in a highly unexpected way is a red flag, even with a seemingly valid basis.
- Embed in Your Privacy Notice: Clearly state which lawful basis you rely on for each processing purpose in your privacy notice. This transparency is a core requirement of the GDPR.
By systematically linking every data use-case to a legal justification, you create a defensible and transparent data governance framework. To understand these legal grounds in more detail, you can explore the various data privacy laws that outline these requirements. Learn more about the legal foundations of data processing.
3. Privacy Notice and Transparency Requirements
Transparency is a cornerstone of GDPR, and your Privacy Notice is the primary vehicle for achieving it. This essential document must provide comprehensive, clear, and accessible information to data subjects about how your organization collects, uses, and protects their personal data. It is not enough to simply have a privacy policy; it must be easily understandable, prominently displayed, and contain all mandatory information required by the regulation.

For African tech startups, a transparent privacy notice is a critical tool for building user trust, especially when handling sensitive financial or personal information. It should explain the “what, why, and how” of your data processing activities in simple terms, moving beyond legal jargon to create a genuine connection with your users. This step is a non-negotiable part of any GDPR compliance checklist.
The Value of a Clear and Accessible Privacy Notice
A well-crafted privacy notice does more than just tick a compliance box; it acts as a declaration of your commitment to user privacy. It empowers users by giving them meaningful control over their data, which reduces complaints and strengthens brand loyalty. It also ensures you are fulfilling your legal obligation under GDPR to inform individuals before or at the time of data collection.
Key Insight: Your privacy notice is a direct conversation with your users. If it’s buried, confusing, or incomplete, you are not only risking regulatory fines but also eroding the trust that is fundamental to your customer relationships.
Leading tech companies like Apple showcase this principle with a layered privacy approach, providing a quick summary upfront with links to more detailed information. This allows users to get the key facts easily while still having access to a comprehensive breakdown. For an African fintech, this could mean providing a concise, icon-driven summary on the app’s sign-up screen, with a link to the full notice in the settings menu.
Implementing Your Privacy Notice Strategy
Your goal is to be as transparent as possible without overwhelming the user. A strategic, user-centric approach is key.
- Use Plain Language: Avoid legalistic and technical terms. Write for your audience, ensuring the notice is clear, concise, and easy to understand for the average user.
- Implement Layered Notices: Present essential information first in a “just-in-time” context or a summary format. Provide links to the full, detailed policy for those who want to learn more.
- Make It Accessible: Ensure your privacy notice is easy to find on your website, app, and any other platform where you collect personal data. It should not be hidden in a footer with a tiny font.
- Test for Comprehensibility: Just as you would with a user interface, test your privacy notice with actual users to see if they can understand it and find the information they need.
4. Data Subject Rights Implementation
Under GDPR, individuals are granted significant control over their personal data. Implementing robust systems to manage Data Subject Rights is not optional; it is a core operational requirement. This involves creating clear, accessible, and efficient processes for handling the eight fundamental rights granted to individuals, including the right to access, rectify, erase, and transfer their data.
For an African fintech company, this means building the infrastructure to respond when a user requests a copy of their transaction history (right of access) or asks to delete their account and associated data (right to erasure). Failing to honor these rights within the stipulated one-month timeframe can lead to severe penalties and a significant loss of customer trust. This makes operationalizing data subject rights a critical component of any GDPR compliance checklist.
The Value of a Streamlined Rights Process
A well-designed system for handling data subject rights is more than a compliance necessity; it’s a competitive differentiator. It demonstrates respect for user privacy and can significantly enhance brand reputation. An efficient process reduces the administrative burden on your teams, minimizes the risk of human error, and ensures you can meet legal deadlines consistently.
Key Insight: Viewing data subject rights as a customer service function, rather than just a legal obligation, can transform compliance into a powerful tool for building user loyalty. An easy and transparent process shows customers you value their privacy.
Leading tech platforms like Facebook and LinkedIn exemplify this with self-service privacy dashboards. Facebook’s “Download Your Information” tool allows users to export their data directly, fulfilling the right to data portability with minimal manual intervention. Similarly, LinkedIn offers a self-service hub where users can access and manage their data, streamlining what could otherwise be a labor-intensive process.
Implementing Your Data Subject Rights Strategy
To begin, map out the entire lifecycle of a data subject request, from initial receipt to final resolution. This ensures a consistent and compliant response every time.
- Implement Self-Service Portals: Where feasible, develop automated, self-service tools that allow users to manage their own data. This empowers users and drastically reduces the manual workload for your support teams.
- Create Standardized Response Templates: Develop pre-approved templates for acknowledging receipt of a request, asking for identity verification, and providing the final response. This ensures consistency and efficiency.
- Train Your Frontline Staff: Your customer support team is often the first point of contact. Provide them with comprehensive training on how to identify, log, and escalate data subject rights requests appropriately.
- Establish Clear Escalation Paths: Not all requests are straightforward. Define a clear procedure for escalating complex cases, such as requests involving third-party data or legal disputes, to your Data Protection Officer or legal team.
- Maintain Detailed Logs: Keep a secure and confidential log of every request received, including the date, the nature of the request, steps taken for verification, and the date and details of the response. This log is essential for demonstrating accountability to regulators.
5. Data Protection Impact Assessment (DPIA) Process
Certain data processing activities carry inherent risks to individuals’ rights and freedoms. The GDPR mandates a proactive approach to managing these risks through a Data Protection Impact Assessment (DPIA). This is a systematic process designed to identify, assess, and mitigate data protection risks before a project or processing activity begins, embedding the principle of “privacy by design” into your operations.
For an African fintech launching a new credit scoring feature using AI or a tech startup deploying biometric authentication, a DPIA is not just a box-ticking exercise. It is a critical risk management tool. It forces your organization to systematically analyze how a new technology or data use case will impact individuals’ privacy, ensuring that potential harms are addressed from the outset, which is a crucial part of any gdpr compliance checklist.

The Value of a Proactive DPIA Process
A DPIA is mandatory under GDPR when processing is “likely to result in a high risk” to individuals. This includes large-scale processing of sensitive data, systematic monitoring of public areas, or using new technologies. Executing a DPIA helps you demonstrate accountability to regulators, build trust with users by showing you take their privacy seriously, and avoid costly design changes after a product has launched.
Key Insight: A DPIA is your organization’s formal risk assessment for privacy. Failing to conduct a necessary DPIA is a significant compliance breach and can result in substantial fines. It shifts your posture from reactive damage control to proactive, responsible innovation.
Prominent examples demonstrate its importance. The UK’s NHS conducted a thorough DPIA for its COVID-19 contact tracing app, publicly documenting the risks and mitigation measures to build public trust. Similarly, a DPIA would be essential for a mobile lending app in Kenya that uses customer transaction data to determine loan eligibility, as this involves automated decision-making with significant effects on individuals.
Implementing Your DPIA Strategy
A DPIA should be a living document, initiated early in any new project’s lifecycle and revisited as the project evolves.
- Consult with Stakeholders: Involve a diverse team including legal, IT security, engineering, and business owners. Their combined expertise is essential for a holistic risk assessment.
- Use Official Templates: Many supervisory authorities, like the UK’s ICO, provide DPIA templates. Using these ensures you cover all the necessary elements required by regulators.
- Document Everything: Clearly describe the processing activity, assess its necessity and proportionality, identify risks to individuals, and detail the measures planned to mitigate those risks.
- Review and Update Regularly: If the nature, scope, or context of your data processing changes, you must review and update your DPIA to ensure it remains accurate.
6. Breach Notification and Incident Response
When a data breach occurs, your response in the first 72 hours is critical. A robust Breach Notification and Incident Response framework is not just a best practice; it is a core, time-sensitive requirement of the GDPR. This involves having a clear plan to detect, assess, respond to, and report personal data breaches to the relevant authorities and, when necessary, to the affected individuals.
For an African fintech processing payments or a tech startup handling user credentials, a breach can be catastrophic for user trust and regulatory standing. The GDPR mandates that organizations notify the appropriate supervisory authority within 72 hours of becoming aware of a breach, unless the breach is unlikely to result in a risk to individuals’ rights and freedoms. This tight deadline makes pre-planning an absolute necessity.
The Value of a Proactive Incident Response Plan
A well-documented and rehearsed incident response plan transforms a potential crisis into a manageable process. It ensures a swift, coordinated, and compliant reaction, minimizing financial penalties, reputational damage, and the impact on data subjects. It moves your organization from a reactive panic mode to a proactive, controlled state.
Key Insight: The 72-hour notification clock starts when you become “aware” of a breach, not when your investigation is complete. A delayed internal reporting process can make compliance impossible, highlighting the need for immediate action and clear communication channels.
The consequences of failing this test are severe. British Airways was fined €22.5 million following its 2018 data breach, partly due to the significant impact on hundreds of thousands of customers. Similarly, Marriott International’s response to the massive Starwood database breach was scrutinized by regulators, leading to a substantial fine. These cases underscore that the response is just as important as the prevention.
Implementing Your Incident Response Strategy
Your plan must be established and tested long before an actual incident occurs. Waiting for a breach to happen before you figure out your response strategy is a recipe for failure.
- Establish Clear Procedures: Document a step-by-step incident response plan that defines roles, responsibilities, and communication workflows. Who makes the call to notify the authorities? Who communicates with customers?
- Train Your Team: All staff, from customer support to engineering, must be trained to recognize a potential breach and know exactly who to report it to internally, without delay.
- Prepare Notification Templates: Create pre-approved notification templates for both supervisory authorities and data subjects. This ensures you provide all necessary information accurately and within the tight timeframe.
- Conduct Post-Incident Reviews: After any incident, big or small, conduct a thorough review to identify weaknesses in your response and security controls. Use these lessons to update and improve your plan.
7. Vendor and Third-Party Management
Your organization’s GDPR compliance is only as strong as its weakest link, and that link is often a third-party vendor. Vendor and Third-Party Management involves establishing comprehensive governance over any external partner, supplier, or service provider that processes personal data on your behalf. This is a critical part of your GDPR compliance checklist because accountability does not end at your company’s firewall.
Under GDPR, your organization (the “data controller”) remains liable for what your vendors (the “data processors”) do with the data you entrust to them. For African tech firms leveraging global SaaS platforms, cloud hosting, or third-party payment gateways, this means you must conduct thorough due diligence and establish contractual safeguards to ensure data is protected throughout the entire supply chain.
The Value of a Robust Vendor Management Program
A structured vendor management program transforms compliance from a contractual formality into an active, risk-based partnership. It ensures that your partners meet the same high standards you set for yourself, protecting you from breaches caused by external vulnerabilities and demonstrating accountability to regulators. This program is essential for building and maintaining customer trust, especially when sensitive financial or personal data is involved.
Key Insight: Simply signing a Data Processing Addendum (DPA) is not enough. You must actively verify and monitor your vendors’ security and privacy practices to ensure they are truly protecting the personal data you share with them.
Global service providers like Amazon Web Services (AWS) exemplify this with their shared responsibility model, clearly outlining the security measures they manage versus those the customer must implement. Similarly, platforms like Slack offer detailed information about their sub-processors and security programs, allowing customers to perform effective due diligence.
Implementing Your Vendor Management Strategy
Start by creating an inventory of all third parties that process personal data for you. From there, you can assess the risk each vendor poses and apply appropriate controls.
- Standardize DPA Templates: Use a robust, standardized Data Processing Addendum (DPA) for all vendors to ensure consistent protection levels and clear contractual obligations.
- Implement Vendor Risk Assessments: Before onboarding any new vendor, use detailed security and privacy questionnaires to evaluate their technical and organizational measures.
- Require Regular Compliance Attestations: Ask key vendors to provide regular proof of their compliance, such as SOC 2 reports, ISO 27001 certifications, or other relevant attestations.
- Establish Clear Incident Notification Requirements: Your contracts must legally require vendors to notify you of any data breach “without undue delay,” allowing you to meet your own reporting obligations.
8. Technical and Organizational Security Measures
GDPR compliance is not just about policies and paperwork; it requires concrete actions to protect personal data from unauthorized access, loss, or destruction. This is where implementing appropriate Technical and Organizational Security Measures (TOMS) becomes a critical part of your GDPR compliance checklist. These measures must be tailored to the specific risks associated with your data processing activities.
Think of TOMS as the digital and human firewall protecting your organization’s most valuable asset: data. For an African fintech processing millions of daily transactions or a health-tech startup managing sensitive patient information, these security measures are the difference between building trust and facing catastrophic data breaches. They encompass everything from encryption and access controls to staff training and incident response plans.
The Value of a Risk-Based Security Approach
A risk-based approach ensures that your security measures are proportional to the threat. It prevents over-investing in low-risk areas and under-protecting high-risk ones. This strategic allocation of resources is crucial for startups and scale-ups operating with limited budgets. It allows you to demonstrate to regulators that your security decisions are deliberate, documented, and appropriate.
Key Insight: Security under GDPR is not a one-size-fits-all solution. Your measures must be “appropriate to the risk,” meaning a company handling public marketing data will have different requirements than one processing biometric or financial data.
Leading tech companies exemplify this principle. Signal’s use of mandatory end-to-end encryption for all communications and Dropbox’s zero-knowledge encryption for certain business plans are prime examples of technical measures designed to mitigate specific privacy risks. For an African tech company, this could mean encrypting user databases, restricting backend access to authorized engineers, and conducting regular vulnerability scans on your mobile application.
Implementing Your Security Measures
Start by conducting a thorough risk assessment to identify potential threats to the personal data you process. This assessment will guide the selection and implementation of your TOMS.
- Implement a Defense-in-Depth Architecture: Don’t rely on a single security control. Layer your defenses with firewalls, intrusion detection systems, encryption (both in transit and at rest), and strong access controls.
- Provide Regular Security Awareness Training: Your staff can be your strongest asset or your weakest link. Conduct mandatory, ongoing training on topics like phishing, password hygiene, and social engineering for all employees.
- Establish Incident Response Procedures: Have a clear, documented plan for what to do in the event of a data breach. This plan should define roles, communication strategies, and steps for mitigation and reporting.
- Document and Review Everything: Keep detailed records of all security measures implemented. Schedule regular reviews (e.g., quarterly) to test their effectiveness and update them as technology and threats evolve.
GDPR Compliance Checklist Comparison
| GDPR Compliance Aspect | Implementation Complexity 🔄 | Resource Requirements ⚡ | Expected Outcomes 📊 | Ideal Use Cases 💡 | Key Advantages ⭐ |
|---|---|---|---|---|---|
| Data Mapping and Inventory | High 🔄🔄🔄 (time-intensive, multi-dept) | High ⚡⚡ (tools, staff across units) | Complete data asset inventory; compliance foundation | Organizations with complex data ecosystems | Identifies risks; supports compliance baseline |
| Lawful Basis Determination and Documentation | Medium-High 🔄🔄 (legal analysis needed) | Medium ⚡ (legal expertise) | Clear legal grounds; transparency to data subjects | All organizations processing personal data | Reduces enforcement risk; clarifies rights |
| Privacy Notice and Transparency Requirements | Medium 🔄🔄 (content & design challenges) | Medium ⚡ (content creation, updates) | Improved user trust; regulatory compliance | Public-facing data collection; websites/apps | Enhances transparency; builds trust |
| Data Subject Rights Implementation | High 🔄🔄🔄 (technical + procedural) | High ⚡⚡ (automation, training) | Empowered users; improved data quality | Customer-facing organizations with frequent DS requests | Demonstrates respect for data rights |
| Data Protection Impact Assessment (DPIA) Process | High 🔄🔄🔄 (specialized, iterative) | High ⚡⚡ (experts, documentation) | Risk mitigation; privacy by design compliance | High-risk processing projects | Proactive risk management; accountability |
| Breach Notification & Incident Response | Medium-High 🔄🔄 (tight timelines, coordination) | Medium-High ⚡⚡ (response teams, tools) | Rapid breach response; regulatory adherence | Organizations handling sensitive/personal data | Minimizes impact; maintains trust |
| Vendor and Third-Party Management | High 🔄🔄🔄 (contracts, monitoring) | High ⚡⚡ (audits, legal counsel) | Supply chain compliance; reduced third-party risk | Enterprises relying on multiple external processors | Extends data protection; clarifies liabilities |
| Technical & Organizational Security Measures | High 🔄🔄🔄 (complex tech and policies) | High ⚡⚡ (security tech, training) | Data breach prevention; compliance with security standards | All organizations with personal data processing | Strengthens overall data protection posture |
From Checklist to Competitive Edge: Embedding Privacy in Your DNA
Navigating the intricacies of the General Data Protection Regulation can feel like a monumental task, especially for dynamic tech and fintech companies across Africa. However, moving through the comprehensive GDPR compliance checklist we have detailed is not merely about ticking boxes to avoid penalties. It represents a fundamental shift in business strategy, transforming a legal obligation into a powerful and sustainable competitive advantage. This journey redefines your relationship with data, placing trust, transparency, and user empowerment at the very core of your operations.
By diligently working through each stage, from initial data mapping to robust incident response planning, you have laid the groundwork for a resilient data governance framework. The key takeaway is that GDPR compliance is not a static, one-time project but a living, breathing component of your organizational culture. It is a continuous cycle of assessment, implementation, and refinement that must evolve in lockstep with your products, services, and the ever-changing global regulatory landscape.
Recapping Your Path to Compliance
Let’s distill the critical journey we’ve covered. Your path to robust data protection hinges on mastering these core pillars:
- Foundational Clarity: Starting with Data Mapping and Inventory (Item 1) and establishing a Lawful Basis (Item 2) creates the bedrock of your entire program. Without knowing what data you hold and why you hold it, compliance is impossible.
- Building Trust Through Transparency: Crafting clear Privacy Notices (Item 3) and engineering seamless processes for Data Subject Rights (Item 4) are your most direct lines of communication with users. This is where you actively demonstrate your respect for their privacy, turning a legal requirement into a trust-building exercise.
- Proactive Risk Management: The Data Protection Impact Assessment (DPIA) (Item 5) is your strategic tool for looking around corners. It enables you to identify and mitigate privacy risks before they materialize, embedding a “privacy by design” ethos into your innovation lifecycle.
- Resilience in the Face of Crisis: A well-rehearsed Breach Notification Plan (Item 6) and rigorous Vendor Management (Item 7) are your safety nets. These processes ensure that when incidents occur, your response is swift, effective, and maintains the trust you have worked so hard to build.
- Securing the Perimeter and Beyond: Finally, implementing strong Technical and Organizational Measures (Item 8) protects the data itself. This is the practical, tangible defense that underpins all your policies and procedures.
The Strategic Imperative for African Innovators
For African tech and fintech leaders, embracing this GDPR compliance checklist is a strategic masterstroke. In a digital economy where trust is the ultimate currency, a verifiable commitment to data protection becomes a powerful market differentiator. It signals to global partners, investors, and customers that your company operates at an international standard, ready for scale and expansion.
Key Insight: GDPR compliance is not a barrier to entry; it is a passport to the global market. It unlocks opportunities in Europe and other regions with stringent privacy laws, future-proofing your business model against the wave of similar data protection regulations emerging across the African continent itself.
This proactive stance moves your organization beyond a reactive, compliance-focused mindset. Instead, you begin to view data privacy as an integral part of your product development and customer experience. This cultural shift fosters innovation, as teams learn to build with privacy in mind from the outset, leading to more secure, user-centric, and ultimately more successful products. Mastering these principles positions your company not just to comply with the law, but to lead the charge as a trusted steward of data in the global digital economy. Your commitment to privacy becomes a core part of your brand identity, attracting discerning customers and top-tier talent alike.
Navigating the complexities of a GDPR compliance checklist while scaling a business requires specialized expertise. OndagoLegal bridges the gap between African innovation and global regulatory demands, providing tailored legal and compliance solutions for tech and fintech companies. Let us help you transform your compliance obligations into a strategic asset for growth.
Learn more about how OndagoLegal can secure your global ambitions.